Prosecute Halifax Bank (CMA)
Donation protected
I'm Paul Moore , an Information Security Consultant from Burntwood in Staffordshire.
Like many Halifax Bank customers, I frequently visit their website to manage my accounts. In 2015, I became aware that Halifax were actively port scanning my device with a view to checking if my PC had been affected by malware. To this day, Halifax continue to perform this unauthorised scan.
Unfortunately, the way in which Halifax go about their checks breaches the Computer Misuse Act. You can read the CMA here , however let me summarise where the breach occurs.
"Unauthorised access to computer material (Section 1.1a/b/c)"
A person is guilty of an offence if --
(a) he causes a computer to perform any function with intent to secure access to any program or data held in any computer
(b) the access he intends to secure is unauthorized; and
(c) he knows at the time when he causes the computer to perform that function that that is the case.
How do they breach the CMA?
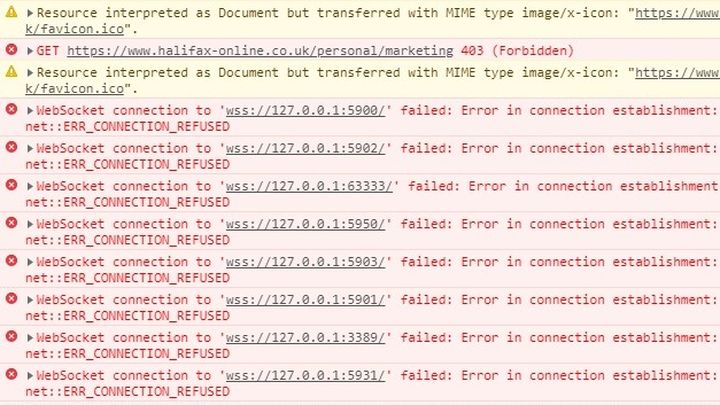
When you visit the "login" page, Halifax actively scans 10 local ports related to remote desktop/VNC. Those ports typically respond if your device allows remote connections; for support purposes etc. However, malware also uses these ports to allow an attacker remote access to your device.

The issue lies in the fact they scan your device *before* you login - meaning you haven't given consent for such a scan. You could land on the Halifax login page via a hyperlink, search result or email link... but until & unless you're a customer, you haven't agreed to their terms, thus any tests performed are entirely without permission and breach CMA.
Why do they perform these tests?
Like many financial institutions, Halifax use a service called ThreatMetrix; software which assists the bank in detecting & mitigating fraud. Whilst their intentions are clear & understandable, the simple act of scanning & actively trying to connect to several ports, without consent, is a clear violation of the CMA.
Let me be clear, Halifax/Lloyds Banking Group are not trying to gain remote access to your device; they are merely testing to see if such a connection is possible and if the port responds. There is no immediate threat to your security or money.
However, the results of their unauthorised scan are sent back to Halifax and processed in a manner which is unclear. If you happen to allow remote desktop connections or VNC, someone (other than you) will be notified as such. If those applications have vulnerabilities of which you are unaware, you are potentially at greater risk.
Have you complained?
I lodged a complaint with Halifax in July 2018 and after several weeks, they responded, denying any wrong-doing and referred me to their privacy policy.



I have subsequently raised this issue with 2 independent solicitors who both agree; their scans breach the CMA and as such, criminal action should be taken.
Turning the tables...
As security researchers, we operate mindful of the CMA. Sometimes, our actions are questionable, other times we clearly overstep the mark if the risk to the public justifies it. However, the question of "intent" arises time & time again.
Some question the need for this criminal action; citing the lack of criminal intent and indeed their responsibility to keep their users safe. However, we've established that consent has not been given... so what if we, as customers, scan the bank's infrastructure to ensure our safety? This would clearly breach the CMA and we'd almost certainly end up in court. The rules should be applied fairly, to both parties.
Reporting to ActionFraud:
I notified ActionFraud, the UK's cyber security reporting centre, on July 5th 2018 and after several hours on the phone, they finally agreed to open a case. However, the required 28 days has passed and ActionFraud have requested a further 2 months to begin looking at the case. At this point, it's unlikely they'll pursue legal action.
Next Steps:
As it looks unlikely ActionFraud will pursue legal action, I intend to launch a criminal investigation directly.
As you can imagine, the costs for such actions can quickly approach 5/6 figures; barristers can cost anywhere from £85-£125 an hour.
This first stage of funding will allow the matter to be discussed with a barrister with a view to deciding how best to proceed. If the barrister disagrees, it may not be financial viable to pursue further action. However, if he/she agrees with our solicitors, this could become a test case which will benefit both the financial & security industry for years to come.
To what end?
Ultimately, I would like one of the following outcomes...
1) Halifax to admit their mistake & pay adequate damages; proceeds from which will be donated to various bug bounty programs & researchers upon which the industry relies.
2) If it's decided to be legal by a barrister/court, the CMA to be revised for clarification; should port scanning arise in any future case.
If you have any questions or would like to discuss this action, please do so via Twitter using the hashtag #halifaxPortScanning
Thank you for reading folks.
Like many Halifax Bank customers, I frequently visit their website to manage my accounts. In 2015, I became aware that Halifax were actively port scanning my device with a view to checking if my PC had been affected by malware. To this day, Halifax continue to perform this unauthorised scan.
Unfortunately, the way in which Halifax go about their checks breaches the Computer Misuse Act. You can read the CMA here , however let me summarise where the breach occurs.
"Unauthorised access to computer material (Section 1.1a/b/c)"
A person is guilty of an offence if --
(a) he causes a computer to perform any function with intent to secure access to any program or data held in any computer
(b) the access he intends to secure is unauthorized; and
(c) he knows at the time when he causes the computer to perform that function that that is the case.
How do they breach the CMA?
When you visit the "login" page, Halifax actively scans 10 local ports related to remote desktop/VNC. Those ports typically respond if your device allows remote connections; for support purposes etc. However, malware also uses these ports to allow an attacker remote access to your device.

The issue lies in the fact they scan your device *before* you login - meaning you haven't given consent for such a scan. You could land on the Halifax login page via a hyperlink, search result or email link... but until & unless you're a customer, you haven't agreed to their terms, thus any tests performed are entirely without permission and breach CMA.
Why do they perform these tests?
Like many financial institutions, Halifax use a service called ThreatMetrix; software which assists the bank in detecting & mitigating fraud. Whilst their intentions are clear & understandable, the simple act of scanning & actively trying to connect to several ports, without consent, is a clear violation of the CMA.
Let me be clear, Halifax/Lloyds Banking Group are not trying to gain remote access to your device; they are merely testing to see if such a connection is possible and if the port responds. There is no immediate threat to your security or money.
However, the results of their unauthorised scan are sent back to Halifax and processed in a manner which is unclear. If you happen to allow remote desktop connections or VNC, someone (other than you) will be notified as such. If those applications have vulnerabilities of which you are unaware, you are potentially at greater risk.
Have you complained?
I lodged a complaint with Halifax in July 2018 and after several weeks, they responded, denying any wrong-doing and referred me to their privacy policy.



I have subsequently raised this issue with 2 independent solicitors who both agree; their scans breach the CMA and as such, criminal action should be taken.
Turning the tables...
As security researchers, we operate mindful of the CMA. Sometimes, our actions are questionable, other times we clearly overstep the mark if the risk to the public justifies it. However, the question of "intent" arises time & time again.
Some question the need for this criminal action; citing the lack of criminal intent and indeed their responsibility to keep their users safe. However, we've established that consent has not been given... so what if we, as customers, scan the bank's infrastructure to ensure our safety? This would clearly breach the CMA and we'd almost certainly end up in court. The rules should be applied fairly, to both parties.
Reporting to ActionFraud:
I notified ActionFraud, the UK's cyber security reporting centre, on July 5th 2018 and after several hours on the phone, they finally agreed to open a case. However, the required 28 days has passed and ActionFraud have requested a further 2 months to begin looking at the case. At this point, it's unlikely they'll pursue legal action.
Next Steps:
As it looks unlikely ActionFraud will pursue legal action, I intend to launch a criminal investigation directly.
As you can imagine, the costs for such actions can quickly approach 5/6 figures; barristers can cost anywhere from £85-£125 an hour.
This first stage of funding will allow the matter to be discussed with a barrister with a view to deciding how best to proceed. If the barrister disagrees, it may not be financial viable to pursue further action. However, if he/she agrees with our solicitors, this could become a test case which will benefit both the financial & security industry for years to come.
To what end?
Ultimately, I would like one of the following outcomes...
1) Halifax to admit their mistake & pay adequate damages; proceeds from which will be donated to various bug bounty programs & researchers upon which the industry relies.
2) If it's decided to be legal by a barrister/court, the CMA to be revised for clarification; should port scanning arise in any future case.
If you have any questions or would like to discuss this action, please do so via Twitter using the hashtag #halifaxPortScanning
Thank you for reading folks.
Organizer
Paul Moore
Organizer